Having completed the basic configuration, the new configuration needs to be saved back to the system. This will very likely require the system to reboot.
After saving the configuration, reload it into IP Office Manager;
•If the IP address settings were changed, you may need to change your PC settings to reload the configuration.
To save configuration changes using IP Office Manager:
1.Click OK to save any changes to the current menu.
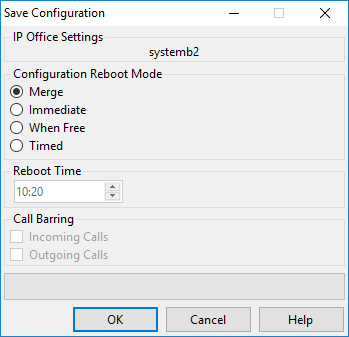
2.Click on the ![]() icon. The Save Configuration menu appears.
icon. The Save Configuration menu appears.
|
•Merge •Immediate •Free •Timed (HH:MM) •Incoming Call Barring •Outgoing Call Barring •! WARNING: This option also bars the making of emergency calls. Therefore, it should be used with caution. |
4.Select the options required and click OK.
Basic Security Configuration
After completing the basic configuration, you should follow the processes in the System Security chapter.